by admin | Jan 14, 2026 | Article, Blog
The Cyber Security Arms Race Just Entered a New Dimension The term “Agentic AI” might sound like science fiction, but for those in the Thames Valley security community, it represents the most significant shift in threat capability since the introduction of...

by admin | Jan 7, 2026 | Article, Blog
The UK’s Digital Security Is No Longer Optional The Cyber Security and Resilience Bill (CSRB), introduced in the UK Parliament on November 2025, marks the most significant shift in UK cyber governance since the 2018 NIS Regulations. This is not just another regulatory...
by admin | Dec 31, 2025 | Article, Blog
December gets most of the attention when it comes to online risk, but the period that follows often carries greater long-term impact. January consistently sees a rise in account breaches, payment disputes, device infections, and privacy issues across the UK. This...
by admin | Dec 24, 2025 | Article, Blog
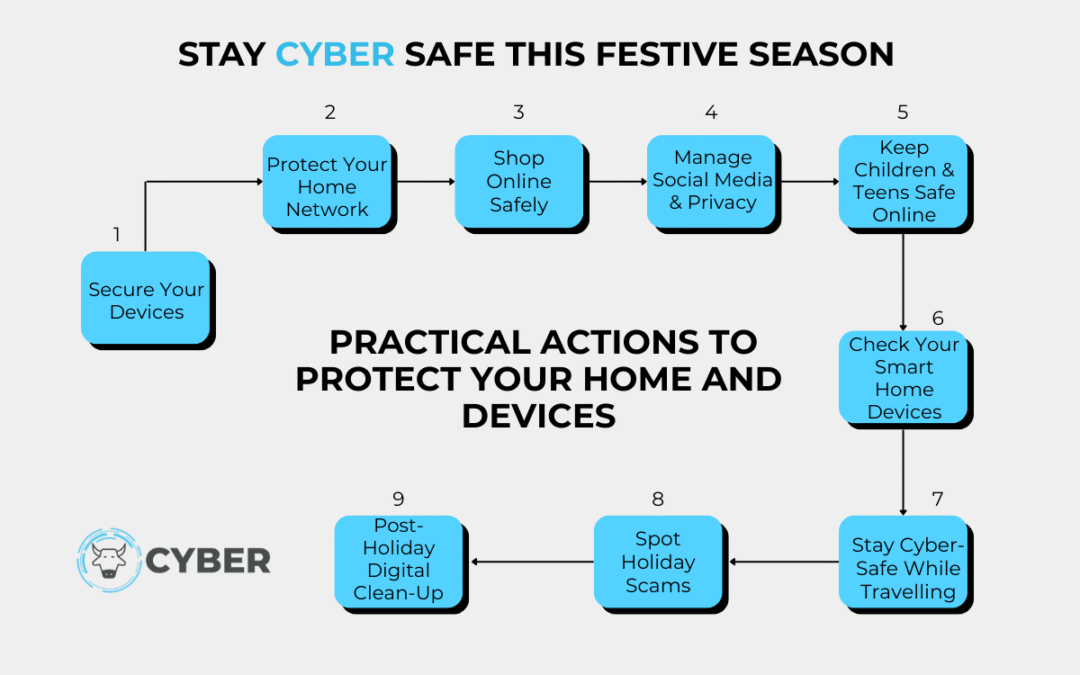
December is one of the busiest digital months of the year. New devices arrive, shopping moves online, travel picks up, and social media lights up. All that activity gives cybercriminals a perfect opening because people are distracted and rushing. Last festive season,...

by admin | Dec 17, 2025 | Article, Blog
Many households welcome guests, relatives, or returning students during December. This creates a unique cyber risk that most people never consider. Every additional person brings new devices, different security habits, and a level of unpredictability that can...

by admin | Dec 10, 2025 | Article, Blog
December is the month when households rely heavily on digital shortcuts. Online shopping peaks, travel arrangements are confirmed, and families switch between laptops, mobiles and tablets more frequently than at any other time of year. All of this creates an appetite...













